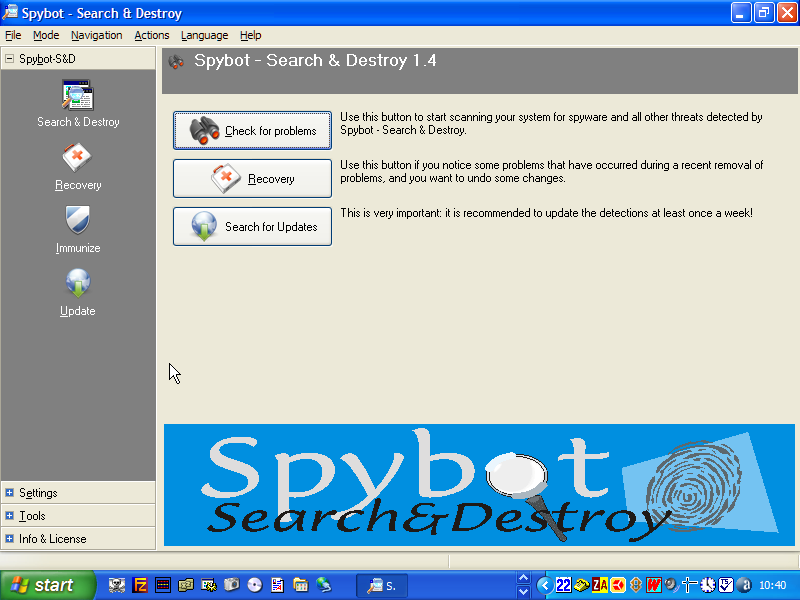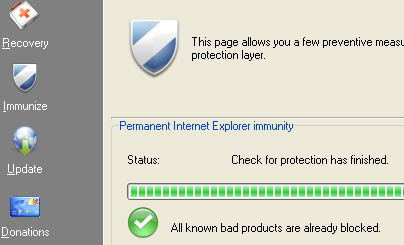
Having updated, it is wise to immunize against
infection by selected spyware.
Click on the Immunize shield to do this. If immunization is necessary
you will be presented with a green cross to tick. This produces the
green progress
bar shown here and indicates how many items need to be added to the
immunization database. It will not always be necessary but is a
valuable check.
Immunity works on Internet Explorer by blocking
installation of executable code from known bad sites, and by
setting known tracking cookies to not be accepted by Internet Explorer.
It is a extra layer of permanent protection beyond that of removing
known spyware. |
The main function of Spybot is to check for problems and remove them from the PC.
At the time of writing Spybot scanned for 39997 known
spyware objects - which can take some minutes, and this figure
increases with every update. Spyware is indicated in red text and each
item will have a check box where it can be selected for what Spybot
calls 'fixing'.
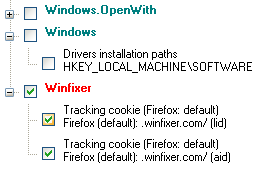
Here is a portion of a scan window showing two spyware tracking
cookies that somehow penetrated my security. The green entries are
usage tracks, left whenever you visit a page with your browser, or just
open any file. These can be useful if you want to open that file
again, and can select it from a list instead of typing the whole filename or
browsing the whole directory structure again, but it also makes that information available to spyware and
Internet attackers. It can certainly do no harm to remove them.
|
We now move on to the Advanced mode that opens up a whole new world
where many may fear to tread. But for those prepared to learn and try
it offers valuable tools. The Settings mode is the first and I will
leave most of it in your hands. But the help file in Spybot
S&D is extensive and easy to follow and I urge you to take some
time reading and following it.
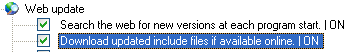
What should be pointed out is that you can update automatically, and this is buried deeply in the Settings subsection of the Settings option. Admittedly it warns and asks:
You should only check this if you are permanently connected to the Internet or if you have a flatrate. Do
you really want to enable auto-checking for updates?
But for most of us on ADSL or broadband these days the answer would have to be, Yes.
|
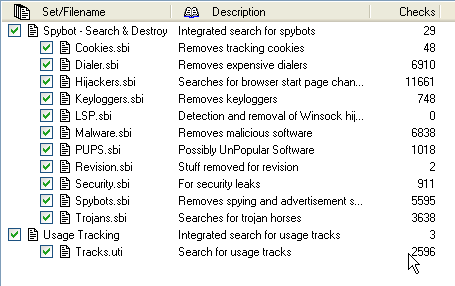
File Sets shows us in detail what we are being protected from and what the program can remove from our system.
Just to take a few of the 39997 items:
* Diallers can make international calls at your expense without your knowledge.
* Keyloggers can read keys as you use the keyboard, reading credit card numbers and much more.
* Trojan horses can infect your system and spread to contacts in your address book.
|
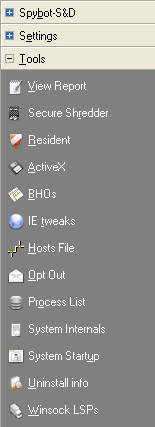
The Tools option is one that is really reserved for experts, but you
can all become experts if you wish and if you have the time.
* Secure Shredder uses pre-defined bit patterns that overwrite files making even hardware recovery
impossible.
* Resident is the browser helper for Internet Explorer that blocks download of files known to be
malicious.
* ActiveX is a Microsoft technology that works only in Internet
Explorer and allows Internet applications that are
more powerful than simple scripts. Spybot will display a green checkmark in
front of ActiveX applications known as legitimate, and a red sign in front of
applications known as illegitimate.
* BHOs are small programs that extend Microsoft's Internet
Explorer. They include visible add-on toolbars in Internet Explorer,
but can also be spyware to display ads or follow your track
across the Internet.
* IE tweaks and Hosts File basically protect against misdirection of the addresses you type into your browser.
* Process List is dealt with below
* System Internals repairs registry entries typically not addressed by other similar programs.
* System Startup is dealt with below.
* Winsock LSPs displays a list of installed network drivers; definitely a reference for
only professionals
|
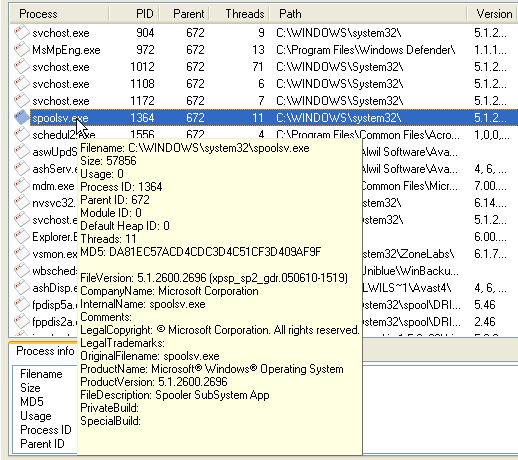
The process list provides a detailed analysis of programs and processes running on your PC.
Processes are the various tasks running on a Windows PC.
Some of the processes are parts of the operating system, while others
are applications automatically launched at startup or manually by the
user - such as Avast, Spybot S&D, Zone Alarm, Outlook Express.
Some of the information is readily digestible; name, path, company, and
description. Other information is more esoteric, but the combination of
all this information is invaluable in determining the integrity and
authenticity of any process.
Take the process I have highlighted. The very reliable source, Process Library, gives this definition:
spoolsv.exe is a Microsoft Windows system executable which
handles the printing process to your local printers. This program is
important for the stable and secure running of your computer and should
not be terminated.
Note: spoolsv.exe is also a process which is registered as the
Backdoor.Ciadoor.B Trojan or the Iambigbrother spyware. The Ciadoor
Trojan allows attackers to access your computer, stealing passwords and
personal data. It is a registered security risk and should be removed
immediately.
So how do I know which one I have? By holding the mouse over the
filename I am presented with the full description of that process on my
PC, and I can see that it is not a Trojan but the genuine article.
|
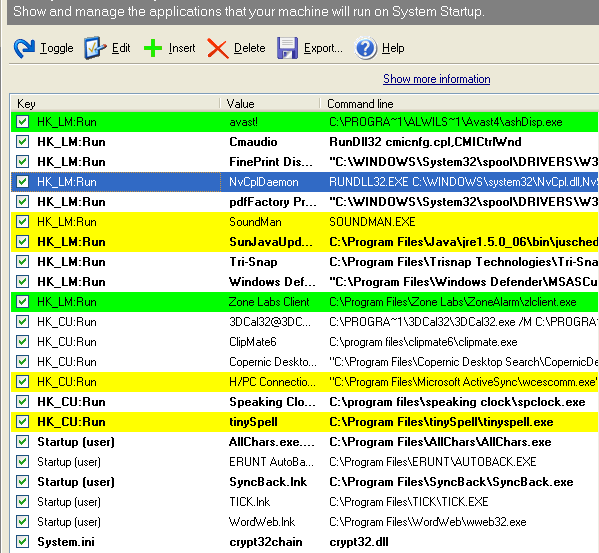
The System Startup tool lists all programs that are started at Windows startup, with some more
information about those of which it is aware.
Programs can be temporarily halted by unticking the relative box, or removed with the delete icon.
The different colours represent:
- Green: legitimate program
- Yellow: unknown, unneeded or unambiguous program.
- Red: malicious program
Spybot will find and identify Trojans and other malware in the
startup list, because many filenames have been hijacked - the same as
in our process list.
Freeware databases cannot always tell you the state of the particular file
on your PC. They know about the genuine file and all the variations,
and will probably rely on file location to classify it. You will see
this especially clarified at www.sysinfo.org that we look at later.
I use Uniblue's Wintasks 5 to positively identify these threats. If you
rely totally on freeware you should check the file location and and use
the filename+location to do a Google search. You will almost certainly
find an entry that puts your mind at ease or else recommends deletion. |
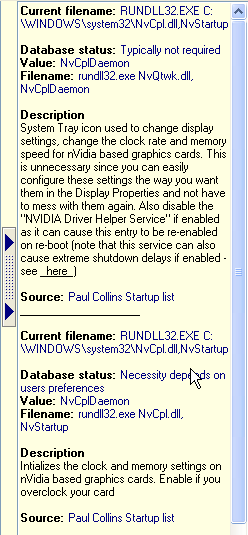
This information actually appears on the right of the image above but
was too big to include that way on any monitor at only 800 x 600
resolution, so I split it.
You can see the comprehensive information and advice available within
Spybot , and hopefully appreciate it enough to use it effectively on
your own PC.
Here you can see if a file that correctly resides in the
Windows\system32 folder is located instead in another folder. In that
case it is almost certainly a Trojan or virus. |